Table of contents
- How Email Works -
- IMAP -
- DNS -
- TCP/IP Model(Transport Layer) -
- Checksum -
- Timers -
- UDP(User Datagram Protocol) -
- TCP(Transmission Control Protocol) -
- 3-Way Handshake -
- TCP(Network layer) -
- Control Plane -
- IP(Internet Protocol) -
- Subnet Masking -
- Packets -
- IPv4 vs IPv6 -
- MiddleBoxes -
- TCP (Data Link Layer) -
- Summary -
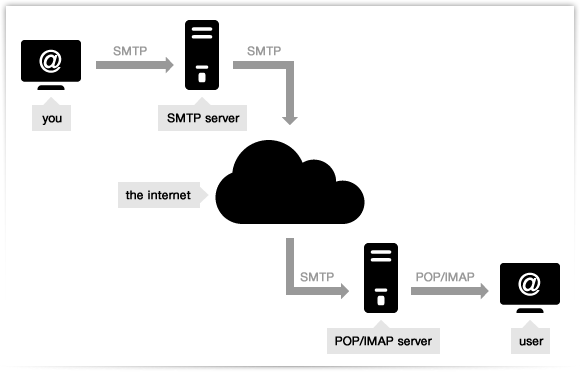
How Email Works -
What is the application layer protocol for email? For sending email is SMTP(Simple Mail Transport Protocol) used to send emails). To receive email you can use POP3(Post Office Protocol). But how the data is going to be transported, which transport layer protocol do we use(TCP/UDP)? Email uses TCP.
nslookup -type=mx gmail.com
#gives detail about the email adress etc
How download emails? POP3 It uses the port 110(maybe)
IMAP -
IMAP( Internet Message Access Protocol) - allows you to view your email on multiple devices. Emails will be kept on the server forever unless you deleted them manually. Local copies will be available on various devices & you can sync all your folders.
DNS -
DNS(Domain Name Service) - Domain names are mapped to IP addresses. We use a service to lookup into these databases. The most popular service for this is DNS. So when you enter google.com It will use DNS to find the IP address of Google's server. How is that a part of the application layer? How does it work? It is very difficult for us to remember the IP address. So that's why we use DNS.
So when you type google.com HTTP protocol is going to take that domain name. It is going to use DNS, DNS converts that URL into the IP address and after that, it connects to the server.
mail.google.com - Here mail - subdomain, google - second level domain, .com - Top level domain.
There are multiple databases for these 3 categories.
When we write google.com
Ist it will check in your computer. So when you visit the website for the first time it stores the value of its IP address that it has found in your local cache/local database on your system. Imagine we are not able to find it in the local cache then it looks at the local DNS server. The local DNS server is the first point of contact. If it is not able find it here. it will check in the root server. The root server said I don't have to check Top level domain, then it goes to ISP, It says no, then it goes to the next Top level domain. Now this will give you the IP address.
You cannot buy a domain, You can only rent it.
[Your ISP has all info about the websites that you visit, doesn't matter you turn on Incognito etc. They know everything]
TCP/IP Model(Transport Layer) -
Transport Layer -
Assume you texting your friend on WhatsApp/Message
Role of Transport Layer - One message being transferred from one computer to another. The transportation part is done by the Network layer. From one computer to another computer this transportation is done by the Network layer. The transport layer lies over the devices. The role of the transport layer is to take the information(whatever message your friend sending from the network to the application). From one Network to another network if data needs to be transferred that part is done by the Network layer. (Actual transportation from one computer to another). But within that computer transportation of the data from the Network to the Application, is done by the Transport layer. The network layer takes care of messages that are delivered from one computer to another. But when the message that delivering from one computer to another, which application do I send the data to? That is done by whom? Transport Layer.
when you courier a box to your friend who lives in another country
![Network Layers Explained: OSI & TCP/IP Models [with examples]](https://www.plixer.com/wp-content/uploads/2018/11/network-layers-2.png)
The transport layer first works on its application then it sends data to the Network layer. Transport layer located? on your Device. The transport layer has protocols - TCP/IP
Assume you sending your friend a file over WhatsApp, VC and File, sending at a particular time.
How does our computer determine how to send these 3 types of data to the network & how will your friend determine when your friend's device has got the data? How will that determine which application to send the data to?
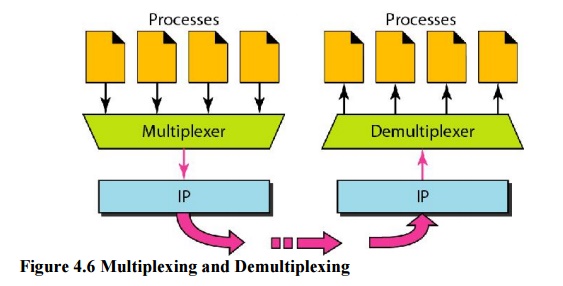
Multiplexing - It allows us to send these all messages/etc things to a lot of destinations. So these three messages are sent to 3 applications/destinations just by one medium. All these things send to Transport layer multiplexes & multiplexes sent to Demultiplexes & then to the user(different data).
Your data is in the bundle.
What do we use to refer to the machine - IP addresses
What do we use to refer to the application - Port Numbers
Sockets - connection/gateways b/w 2 application
If the Message application wants to send the message to another application. It gives it to the Sockets. This Socket has port Numbers. Data travel in packets. The transport layer attaches these Sockets Port numbers. That is why it knows, where the application data coming from & to which application needs to send data.
The transport layer takes care of Congestion Control(Traffic). For eg - The network has lower bandwidth & you send the data packet so rapidly. Some packets will get lost known as Congestion. So it tries to send packets at a slower rate Congestion control algorithm built-in TCP.
Checksum -
You send data from the network layer to the network layer. Something may be possible that data get corrupted in between. So the transport layer takes care of this by Checksum.

When you send the data checksum is calculated using this data. When you send the data you will attach the checksum that you calculated on your own & when your friend receives the data they will also calculate the checksum using some algorithm. If the value is different, then something is gone wrong, and if the value is correct means data is sent successfully.
Timers -
How would I know that my packets have been received by my friend? Something is known as Timers.
Timers are used to avoid excessive delays during communication. When a sender sends a segment to the receiver, a timeout timer starts. If the ACK gets received before the timer expires, then nothing happens. Otherwise, the segment is considered lost, and therefore, it needs to be transmitted again. Thus, it is resent, and the timer restarts.
Imagine that you are sending something to your friend. You send data packet no. 1, you start the timer then your friend got packet no.1, and you end the timer. Now you send packet no. 2 & start the timer and after it reaches your friend, he gives info back to you between this packet gets lost and the timer expires. You treated that he didn't receive the packet no. 2. And then he tries to send packet no. 2 again. Now your friend has 2 packet no. 2(duplicate).
How we solve this problem? We solve this problem using sequence numbers. A unique value number will be provided for every segment packet.
UDP(User Datagram Protocol) -
What are the transport layer protocols? TCP/UDP
What are the application layer protocols? HTTP etc
What are the Network layer protocols? IP
In UDP -
Here your data may/may not be delivered 100%
Data may change on the way
Data may not be in the order
connectionless protocol(which means no connection will be established between two computers & they still be able to send the data
UDP uses checksums still it does not care about the data being transferred to another user 100%.
UDP packet - Every data packet will have a port number(your port number and your friend's port number)
Why do we use UDP? Because it is faster.
Where do we use UDP?
Video calls
DNS uses UDP
Gaming
To see data packets coming into your computer
sudo tcpdump -c5
TCP(Transmission Control Protocol) -
We know that TCP uses in HTTP.
Transport Layer Protocol-
When you get the data in the transport layer from the application layer. So you know data you get in segments. The application layer sends lots of raw data & TCP segments dividing this data into chunks and adding headers. It also collects the from the Network layer. At the receiving end of your friend, this divided data combine and send to your friend. It also provides congestion control. It takes care of 2 things - when data does not arrive, maintaining the order of data.
The email application layer protocol uses SMTP, POP and IMAP - This application layer protocol uses a Transport layer protocol called TCP.
FEATURES -
connection-oriented
also provides error control
congestion control
Full Duplex
Two computers are connected. You can send files from computer A to computer B. Computer B can send files also you both can send files simultaneously. Using TCP there can only be 2 end points. You cannot send 1 message to 10 computers. 1 TCP connection only between 2 computers.
3-Way Handshake -
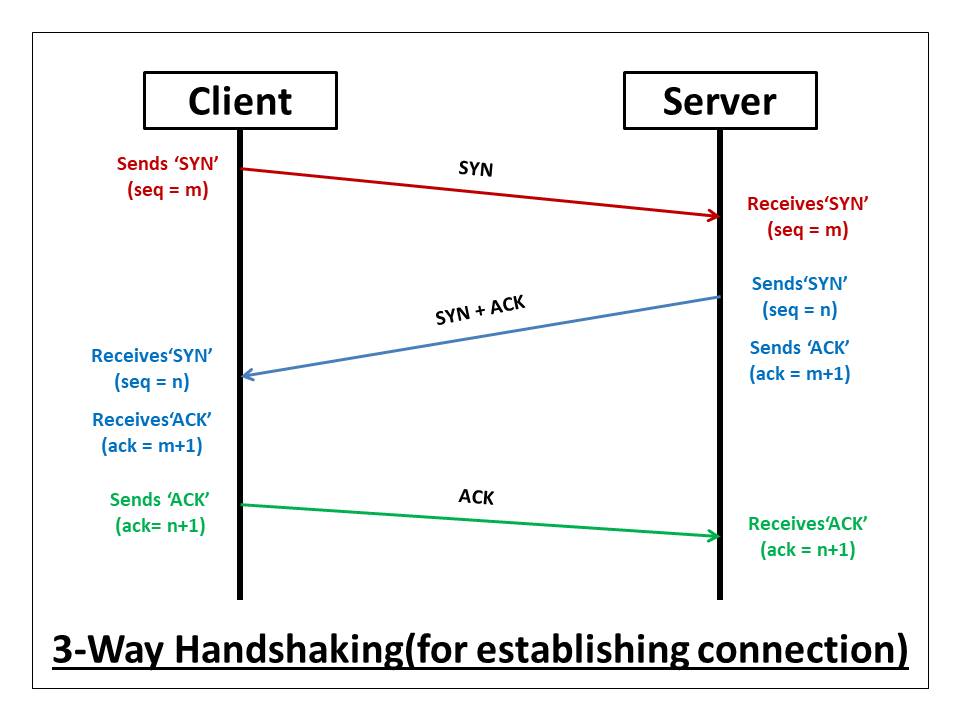
When you send a connection request to the server. You are going to send a flag called the Synchronization flag. It means a new connection is being established. It's just a place value inside headers. The server now be like oh I got Synchronize flag. Also, send it with the sequence number(So we know it's in order). Sequence numbers are random numbers because if the sequence will not be random then it will easy to guess and anyone could be able make a connection with the server & hackers could take advantage of it. So for security purposes sequence numbers are random. Now the server is like I got the 'SYN' flag & I send you the syn flag + ack flag. This is a 3-way handshake.
TCP(Network layer) -
We know that the application layer sends the data to the transport layer. So the data that is in the transport layer, the data we have in segments. In the network layer data is in the packets, Data link layer - data in frames.
So what works at the Network layer - Routers.
Here we work with routers.

You have to send data from computer A to computer B. So many routers are connected in between /to each other. Every single router has its network address. The network address allows us to send data packets. So Network 1 is going to check in its Routing table/Forwarding table that consists of every destination address. The packet contains the network layer address of the destination. It will contain the network layer address who is sending it & what information you want to send. So when you try to send packet A to next this will check the forwarding table and be like - oh, I receive this packet & this packet needs to be sent to this particular location. Let me check my forwarding table and then it tells the destination(This is forwarding table. This is hop-by-hop forwarding. Hopping router to router until it reaches the correct router. Forwarding and routing lie inside Routers.
The forwarding table comes inside the routing table. The routing table may have multiple paths. The forwarding table contains only 1 path(much faster) Exist inside the routers. The forwarding table is a link data structure.
192.168.2.80 - 192.168.2(Network address), 80(device address).
Control Plane -
The control plane is part of a network that controls how data packets are forwarded — meaning how data is sent from one place to another. The process of creating a routing table, for example, is considered part of the control plane. Routers use various protocols to identify network paths, and they store these paths in routing tables.
Two types of Routing -
1) Static Routing:
Static Routing is also known as non-adaptive routing which doesn’t change the routing table unless the network administrator changes or modifies them manually. Static routing does not use complex routing algorithms and It provides high or more security than dynamic routing.
- Dynamic Routing:
Dynamic routing is also known as adaptive routing which changes the routing table according to the change in topology. Dynamic routing uses complex routing algorithms and it does not provide high security like static routing. When the network change(topology) occurs, it sends the message to the router to ensure that changes then the routes are recalculated for sending updated routing information.
IP(Internet Protocol) -
Network layer protocol? IP. What is IP? Protocol lies in the Network layer.
IPv4 - Internet Protocol version 4 - 32 bit number
IPv6 - Internet Protocol version 6 - 128 bit
IP address - 5.6..9.14 (5= 8 bit, 6 = 8 bit and so on..)
5 in binary - 00000101
Hopping happens over the ISP. Is the router take part in hopping? No. So what happens is instead of hopping on the individual router. This Hopping thing happens over the ISP. The routing table & etc do not have every single person's information in every single router in the world. The basic idea is, it has blocks of addresses(IP). These blocks of IP addresses are assigned to ISP known as Subnetting.
192.168.2.30 - Here '30' is the Host address and '192.168.2' - is the Subnet address.
A subnet or subnetwork is a smaller network inside a large network. Subnetting makes network routing much more efficient.
So whenever a router will forward a packet it should know the subnet of the destination. So internet society added classes for this.
Classes of IP Addresses -
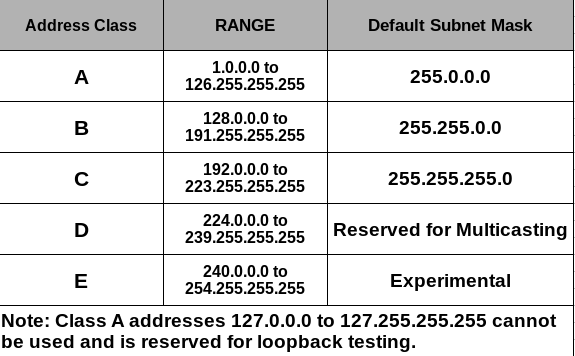
Subnet Masking -
A subnet mask is a 32-bit number created by setting host bits to all 0s and setting network bits to all 1s. In this way, the subnet mask separates the IP address into the network and host addresses.
The subnet mask for class B is 255.255.0.0. Here 255.255 - Subnet address and 0.0 - Host address
Variable Length Subnet - You can set the length of the subnet network. for eg -
127.0.0.0/31 - first 31 bits are occupied by the subnet mask
Reserved Address -
127.0.0.0/8
means 1st 8 bits are reserved & 0.0.0 can be anything.
for e.g 127.0.0.1
These are loopback addresses. Because the process that is going to be running on your machine uses TCP/IP protocol. It will allow you to contact the same process. So your device acts as a client and server also. It will never be down.
Packets -
Apart from the data, the Header is 20 bytes.
Header - 20 bytes containing IP version, total length, identification no., flags, protocols, checksums, TTL, addresses etc.
What is TTL? Time to live (TTL) refers to the amount of time or “hops” that a packet is set to exist inside a network before being discarded by a router.
ping google.com
#here you see the TTL 60 ,69 etc sequence no. also shows here
IPv4 vs IPv6 -
IPv4 - 32-bit number (4.3 billion addresses unit)
IPv6 - 128-bit numbers
Representation -
8 digit number(every single number is a hexadecimal digit) represents 16 bits part of the address
MiddleBoxes -
Middleboxes interact with the Network packet that comes from the network layer. A middlebox is defined as any intermediary device performing functions other than the normal, standard functions of an IP router on the datagram path between a source host and a destination host.
fireball -
connected to the Global internet
your trusted network
Filter out IP packets based on various rules.
Addresses
Modify packets
Port numbers
Flags
Protocols
fireball - provides us filter(all IP packages coming to my network address can be filtered out based on address/port no etc.
Two types of fireball
Stateless fireball - Do not maintain the state
Stateful fireball - sees the packet and maintains the state(Stores it in the cache memory). Since it uses cache memory it is a little bit more efficient.
Network Address Translation (NAT) -
It is a method of mapping one IP address space into another by modifying the Network address IP information in the header of the packet.

Why is this happening?
To slow down the consumption of IP addresses. The source address of the packet that you have is replaced by a public address. Then checksum is also updated and carried out by TCP & UDP.
TCP (Data Link Layer) -
Data packets that we received from the Network layer. The data link layer is to send these packets over the physical link. It transfers your data between devices. For eg - you have your router, and your router has some IP address provided by your ISP. Some devices are connected to your router. These devices have their IP addresses. There's a subnet available over here & a new IP address is going to allocate this. How did this happen? By using DHCP(Dynamic Host Configuration Protocol). So when a new device is added/connected. It will connect your new device 1 connect to the DHCP server & every DHCP server has a pool of IP addresses. From there the IP address assigns to the new device.
There are many devices connected to LAN. Every 2 computers are being found out together using IP address/subnet of IP. But the data link layer communicates with each other using the Data link layer address something known as the data link layer address. So every device that has an IP address also has a Data link-layer address. So if you send something from one computer to another know the data link layer destination also. You can manually allocate data link layer addresses to devices but it also happens sometimes automatically. for eg - devices connected to one LAN.
Let's assume device 1 wants to send something to device 4. So device 1 will check it in its cache - hey, do I have the data link layer address of device 4? It says, No. When it does not have it, it is going to ask all the devices that are connected to this same network. All the devices connected to this network will receive a message from device 1. What is the message? The message will be a packet/a frame. This is known as ARP(Address Resolution Protocol) cache.
Frame Contains - Data link layer address of sender & IP address of the destination.
When you make a request & data comes back to your router. The router attached the correct private IP address to the data packet ensuring that they got to the computer &device. The router will do this because all those private address we talked about actually correspond to the correct MAC address. The router will assign the IP address/MAC address to it to make sure reaches the current particular device. So since the public & private IP address will remain the same but MAC address keep on changing as the data will travel from one device to another. MAC address - 12-digit alphanumeric digits are called Media Access Control. It's a unique identity for a particular interface. It is used in all technologies like ethernet, wifi, Bluetooth etc. So you can block some devices using the MAC address.
You Completed This Chapter Of Networking 🎊.

Summary -
Here we see - How email works(SMTP, POP3, IMAP), DNS, TCP/IP model (Transport layer), Checksums, Timers, UDP, Control Plane, Subnet Masking, Packets, IPv4/IPv6, Middleboxes, NAT and TCP(Data Link Layer).

